Streaming MP4 files with Apache + h264_streaming has never been easier. Setup your web server to stream MP4 files using Apache in just 3 minutes.
cd /usr/local/src
wget http://h264.code-shop.com/download/apache_mod_h264_streaming-2.2.7.tar.gz
cd mod_h264_streaming-2.2.7
./configure --with-apxs='which apxs'
make && make install
Non WHM/cPanel users
Should now add those two lines into httpd.conf:
LoadModule h264_streaming_module /usr/local/apache/modules/mod_h264_streaming.so
AddHandler h264-streaming.extensions .mp4
and simply restart Apache using:
service httpd restart
WHM/cPanel users
Should use Include Editor since any changes made to httpd.conf will be lost in case of rebuilding apache.
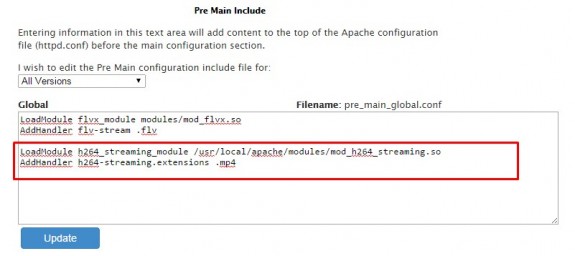
So login to WHM and go to Apache Configuration -> Include Editor -> Pre Main Include -> All Versions and in the box that appears copy/paste following two lines and after saving that confirm Apache restart.
LoadModule flvx_module modules/mod_flvx.so
AddHandler flv-stream .flv
Here are a few pictures for newbies so they can find their way trough more easily:
1. Apache Configuration
2. Include Editor
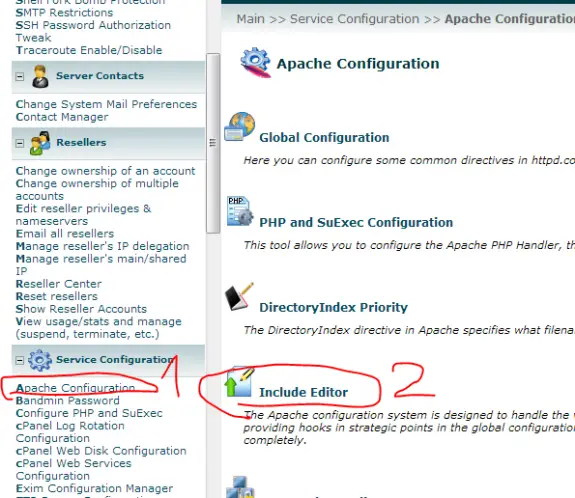
3. Locate PreMain Include – select All Versions
4. Copy/paste those two lines and press Update (then confirm Apache reload)
That’s it!
FLV Streaming using Apache
To learn how to setup FLV streaming using Apache click here
I’ve seen numerous DigitalOcean vs Linode reviews but for some reason people always made these tests with the cheapest plans. For my review and my tests I’ve decided to use slightly bigger plans – with 8GB of RAM on both – and see what comes up. Both plans are priced at $80/month (billed hourly). Before we go take a quick note on the terminology: a DigitalOcean VPS is called a “droplet” while Linode’s one is called a “linode” 🙂
Offer
DigitalOcean offers:
– 8GB or RAM
– 4 CPU cores
– 80GB of SSD disk space
– 5TB of bandwidth
– 1Gbps network connection
Linode offers:
– 8GB of RAM
– 6 CPU cores
– 192GB of SSD disk space
– 8TB of bandwidth
– 1Gbps network connection
So clearly Linode offers more for the same price: more than a double of disk space, 2 more CPU cores and more bandwidth. This is probably due the fact that they have released their offer after DigitalOcean so that’s some healthy competition right there.
Hardware
Before we start let’s talk a bit about hardware used by those two companies. DigitalOcean at Amsterdam NL (AMS-3) droplets use Intel Xeon E5-2630L v2 at 2.4 GHz. On the other hand a Linode at London shows Intel Xeon E5-2680 v2 at 2.80GHz. So Linode should have a slightly better processor and should get more processing power for the same amount of money. Other than processor, there isn’t a way to detect the type of memory or SSD drives used.
Note: DigitalOcean at Netherland’s AMS-1 location “hides” their CPU model behind “QEMU Virtual CPU version 1.0” clocked at 2 GHz. So this is one more reason to choose AMS-3 over AMS-1.
Virtualization
DigitalOcean utilizes KVM virtualization while Linode uses Xen.
Control Panel
While DigitalOcean have a minimalist approach to their control panel it lacks some important functions: for example you can’t see how much bandwidth have you spent (not that they care since they do not charge if you go over the monthly limit), you can’t have more than one IP allocated to a single droplet, plan upgrades and downgrades can be really complex to do and time consuming creating a significant downtimes.
Linode is clearly more feature rich platform. They will provide you much better charts and more options. Their Control Panel is more geeky and their SSH in web console works much better and faster compared to one at DigitalOcean, you can buy and assign extra IPs to your linode, you will get an email if your linode is under high load and it can be even auto rebooted in case it hangs.
Aditional Services
DigitalOcean offers backups at the cost of +20% on the droplet monthly price. They also offer free DNS hosting and that’s about it. Linode offers backups (at the same price +20%) and free DNS hosting but beside that they also offer some interesting features like Monitoring, Load Balancing and Fully Managed Service (at $100/month per account for all liodes you have).
OS Choices
DigitalOcean offers CentOS, CoreOS, Debian, Fedora, Ubuntu as well as preinstalled applications (Ruby on Rails, WordPress, LAMP, LEMP, Django, MEAN, NodeJS, Ghost, GitLab, Docker, Drupal, Dokku, Magento, Redmine). Linode offers: Arch Linux, CentOS, Debian, Fedora, Gentoo, openSUSE, Slackware, Ubuntu but they also offer lot more settings when creating a new Linode (from partition setup to kernels).
Setup Time
DigitalOcean is clearly a winner: they will have your droplet created in 55 seconds and process is really easy. While the same thing on Linode takes few more minutes and is somewhere complicated: you first create a new linode and then deploy an OS while at DigitalOcean it’s done at once.
Geo Locations
At Linode you can deploy at United States (Dallas TX, Fremont CA, Atlanta GA and Newark NJ), United Kingdom (London) and Japan (Tokio) while Digital Ocean on the other hand offers droplets at United States (New York NY, and San Francisco CA), United Kingdom (London), Netherlands (Amsterdam) and Singapore. Linode has better offer of locations in US but they lack Netherlands as really important European location.
Uptime and Stability
I’ve been using DigitalOcean since Feb 2013 and I haven’t noticed any major downtime. In case of some works or scheduled maintenance they send on time emails and they really keep the downtime minimal. I’ve been using Linode for a few months and they also seem stable and reliable. So they are both stable and unlike many people claim that they would never host “mission critical” stuff on DigitalOcean for a reason, I’m doing exactly that since Feb 2013 without any problems. Even this site is hosted on DigitalOcean since then.
Support
In the start DigitalOcean support was really helpful bur recently the quality of their support is bit lower, but on the other hand they offer amazing amount of tutorials and really a helpful community. Linode is famous for their good support and I’ve also found really really helpful community on their IRC (almost like a unofficial live chat support).
Performance
Linode should have better performance than DigitalOcean because of the more powerful processor and more cores available. But is faster? Well, actually no! I’ve used ServerBear’s benchmarks (one newly created CentOS 7 dorplet/linode) and here are the results I’ve got:
Linodes single core UnixBench score is 516.6 vs 1,235.7 for DigitalOcean. At a single core level a DigitalOcean is almost twice faster than Linode. This is really interesting and totally unexpected result!
But Linode has 6 cores and DigitalOcean has only 4 so it will be faster anyway, right? More cores means more power, right? WRONG!!!
Even though DigitalOcean has 50% less cores their total score is 50% better than Linode’s (2,154 compared to 3,356) meaning that every single DigitalOcean CPU core performs 100% faster than every single Linode’s core. And that’s another unexpected result! This is also very odd and might suggest that Linode is oversold or something but I’m really not sure.
If you don’t trust me take a look at the results your self:
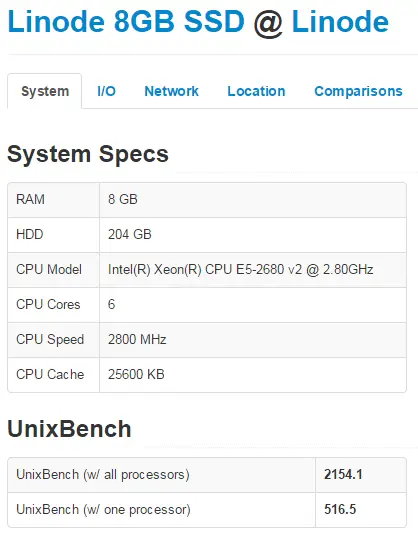
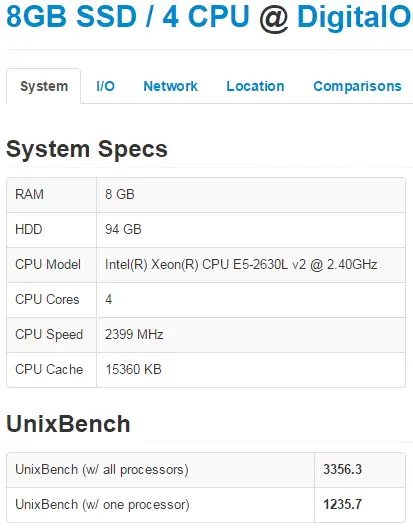
What about IO performance? Who’s got faster SSDs? My results show that read performance is pretty close while write performance almost twice faster on Linode:
DigitalOcean:
Timing cached reads: 16442 MB in 2.00 seconds = 8233.03 MB/sec
Timing buffered disk reads: 1070 MB in 3.00 seconds = 356.62 MB/sec
Linode:
Timing cached reads: 18408 MB in 1.98 seconds = 9298.57 MB/sec
Timing buffered disk reads: 2142 MB in 3.00 seconds = 713.35 MB/sec
But, ServerBear tests show that Linode IO is way much faster:
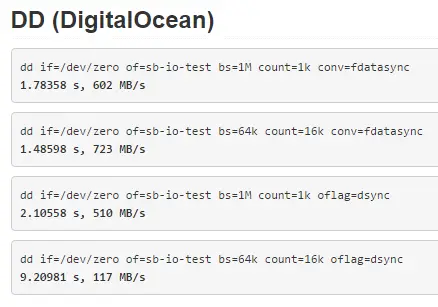
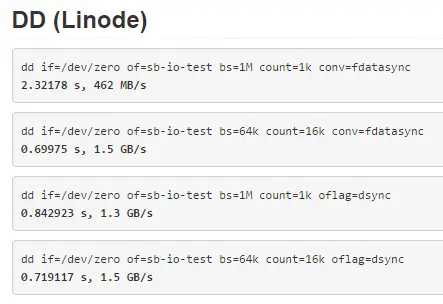
Network speeds are pretty close so we can call them even.
Complete Benchmark Results
Click on a links below for complete benchmark results:
– DigitalOcean: http://serverbear.com/benchmark/2014/11/29/GCJgYYuCapGFxUfV
– Linode: http://serverbear.com/benchmark/2014/11/29/bffAscAzM9j8mZSl
Conclusion
Things aren’t always as they might seem. Even Linode has slightly better processor and twice more cores my benchmark results showed that it’s not faster than DigitalOcean. In fact it’s almost 50% slower. On the other hand Linode IO performance of is twice (or more) times better than IO performance of DigitalOcean.
My Recommendation
Even both are really good hosting providers and they give a lot for the money I couldn’t say one host is better than another. But here are some general guidelines I came up with that might help you decide:
- If you need simple and cheap VPS to play around – DigitalOcean
- If you need fast CPU or you are hosting CPU intense application – DigitalOcean
- If you need to deploy WordPress, Drupal, Redmine, LAMP or LEMP application – DigitalOcean
- If you plan on serving lots of static content – Linode
- If you need lots of disk space – Linode
- If you need lots of geeky (*nix) functions – Linode
- If you like minimalist (Apple) approach – DigitalOcean
- If you want it managed and don’t mind paying extra $100/month – Linode
- If you need more than one IP – Linode
- If you need lots of bandwidth – Linode gives more but DigitalOcean doesn’t charge for overage 😉
- If you need to scale up (or down) your plan easily – Linode
In the end – whichever you pick – you’ll be happy with it since they are both really good virtual hosting providers. Compared to regular (non SSD powered) VPS hosts they are both really fast.
While monitoring my system I have notices increased number of requests to xmlrpc.php. Every single of those requests took 200MB to 205MB of ram and resulted in system instability and in few occasions it caused my 8GB Digital Ocean Droplet to go out of memory and eventually crashed leaving all my sites not working for some 10hours or so.
Recently I’ve read that many hackers now use xmlrpc.php instead of wp-login.php to execute their brute force attacks. And the problem is – since WordPress 3.5 you can’t disable the use of xmlrpc, at least not from the WordPress control panel.
There are many ways to do that and I’ll write some:
1. Deleting xmlrpc.php file
This is really not recommended. Also after WordPress (auto)update the deleted file will be replaced so it’s not really smart to do this, but I just wanted to write this just in case someone doesn’t try to do this.
2. Plugins
There are several plugins that can do this. I found these two to be the most used ones: Disable XML-RPC and XML-RPC Pinkback. Both plugins are really basic (only couple lines of code) but they should be able to help you out and protect your blog against those attacks.
3. Adding filter to theme functions.php file
This is basically same thing as the plugin above, but you have one plugin less. All you need to do is to edit your theme’s functions.php and add these couple of lines:
function remove_x_pingback($headers) {
unset($headers['X-Pingback']);
return $headers;
}
add_filter('wp_headers', 'remove_x_pingback');
add_filter('xmlrpc_enabled', '__return_false');
4. Block access at .htaccess
You can simply add this one line of code to your .htaccess file and block the access to the xmlrpc.php file entirely. User accessing the xmlrpc.php will get the 403 Forbidden error.
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
5. Blocking access in nginx
If you are running nginx instead of Apache you should add this code to your nginx configuration:
server {
location = /xmlrpc.php {
deny all;
}
}
6. Block on entire server
If you have one server or VPS with tens of hundreds of WordPress installations (like me) any of the solutions above will take time to implement. So the best thing to do is to block access to xmlrpc.php file on Apache level, simply by adding this to httpd.conf file:
<FilesMatch "^(xmlrpc\.php)">
Order Deny,Allow
Deny from all
</FilesMatch>
Or even better adding this code (that also blocks wp-trackback.php and also prevent’s trackback hacking attempts).
<FilesMatch "^(xmlrpc\.php|wp-trackback\.php)">
Order Deny,Allow
Deny from all
</FilesMatch>
If you don’t use XML-RPC than you can safely disable it using any of the methods above (except the first one, of-course) and protect your blog against xmlrpc hacks.
Few days ago I noticed the following error at CSF:
WARNING: RESTRICT_SYSLOG is disabled. See SECURITY WARNING in Firewall Configuration
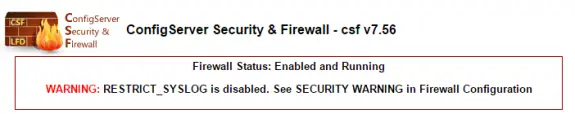
Here is easy solution how to solve this:
1. Login to WHM
2. Home > Plugins> ConfigServer Security & Firewall > Firewall Configuration
3. Set RESTRICT_SYSLOG to 3 (which is the default value), save and restart CSF
Thats it!







